This is the final post of a 7 part post on managing vSphere 5 Certificates:
- Installing a Root Certificate Authority
- Distributing the root CA certificate to clients
- Creating the default vCenter 5 Server Certificate and including a DNS alias
- Replacing the default vCenter 5 Server Certificate
- Replacing the default vCenter 5 Web Client Server Certificate
- Replacing the default vCenter 5 Inventory Service Certificate
- Replacing the default Update Manager 5 Server Certificate
VMware Update Manager uses a different self-signed certificate to authenticate against vCenter Server which also needs to be replaced. You can use the same vCenter certificate if the Update Manager installation is on the same server as vCenter or create and trust a new certificate using the same procedure with the Update Manager server name if it is on another server.
On the Update Manager Server navigate to the Update Manager installation directory C:\Program Files (x86)\VMware\Infrastructure\Update Manager.
Make a backup copy of the SSL folder.
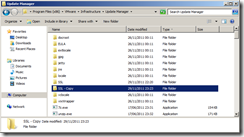
Copy the same rui.crt, rui.key and rui.pfx certificate files you created as part of the vCenter Server certificate process into the SSL folder if Update Manager is on the same server else use the other ones you have created.
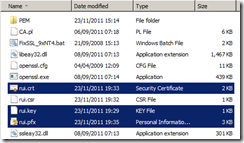
Read more…
This is part 3 of a 7 part post on managing vSphere 5 Certificates:
- Installing a Root Certificate Authority
- Distributing the root CA certificate to clients
- Creating the default vCenter 5 Server Certificate and including a DNS alias
- Replacing the default vCenter 5 Server Certificate
- Replacing the default vCenter 5 Web Client Server Certificate
- Replacing the default vCenter 5 Inventory Service Certificate
- Replacing the default vSphere Update Manager 5 Server Certificate
You should now have a root CA certificate distributed to all clients so you can proceed with creating certificates for vCenter 5 which will be trusted by this root CA certificate. These steps will also allow you to create DNS aliases for your certificate if you need them so you can connect to your vCenter server using any of the aliases and still have a valid certificate.
In order to create certificates you will need an application to generate them, one of the easiest is OpenSSL.
Installing OpenSSL
If you install OpenSSL on a vCenter Server, as vCenter 5 only installs on 64-bit you should download the 64-bit version of Win64OpenSSL_Light-1_0_1b and its pre-requisite Visual C++ 2008 Redistributables (x64)
Install Visual C++ 2008 using all default settings.
Read more…
This is part 2 of a 7 part post on managing vSphere 5 Certificates:
- Installing a Root Certificate Authority
- Distributing the root CA certificate to clients
- Creating the default vCenter 5 Server Certificate and including a DNS alias
- Replacing the default vCenter 5 Server Certificate
- Replacing the default vCenter 5 Web Client Server Certificate
- Replacing the default vCenter 5 Inventory Service Certificate
- Replacing the default vSphere Update Manager 5 Server Certificate
The posts will
Once you have installed the Root Certificate Authority (CA) you may need to distribute the root certificate to clients. The root CA certificate needs to be in the Trusted Root Certification Authorities certificate store on all clients who need to access vCenter for the certificate trust chain to work. If you are not using your own root CA and have used a commercial root CA this certificate is most likely already in your certificate store.
If the root CA is installed using Active Directory Certificate Services on a server that has access to the Active Directory directory service, the root authority’s certificate will automatically be placed in all users’ Trusted Root Certification Authorities certificate store. This means the distribution of the root CA is taken care of by AD and there’s nothing more you need to do.
As I have installed Active Directory Certificate Service on a domain controller with Domain Admin credentials this distribution has taken place. You can check this by going to any server or workstation within the trusted domain forest and after doing a reboot just to ensure the certificate has had time to be copied down check the Trusted Root Certification Authorities list and see if there are certificates in the list for your own CA. In my example you can see that there are two Self-Signed for lab.int certificates in the list so the deployment has been successful.
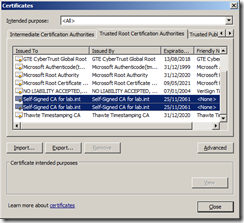
Read more…
Updated: 27 February 2012 to include vCenter 5 Web Client Server and vCenter 5 Inventory Service
This is the first part of a 7 part post on vSphere 5 Certificates:
- Installing a Root Certificate Authority
- Distributing the root CA certificate to clients
- Creating the default vCenter 5 Server Certificate and including a DNS alias
- Replacing the default vCenter 5 Server Certificate
- Replacing the default vCenter 5 Web Client Server Certificate
- Replacing the default vCenter 5 Inventory Service Certificate
- Replacing the default vSphere Update Manager 5 Server Certificate
The posts will take you through building your own certificate trusting infrastructure and distributing the certificates, creating your own vCenter and Update Manager certificates which can also include DNS aliases and all the steps required to put it all together.
Managing certificates is one of the aspects of a virtualisation environment that is often overlooked or even avoided as it is seen as a hassle and having secure certificates is often not a core requirement of your virtualisation infrastructure.
However there are reasons why you may need to have certificates installed within your environment. Many financial companies, government departments or security sensitive installations require trusted certificates to be installed due to legal regulatory requirements. Public cloud providers need to ensure they are exposing their cloud in a trusted and secure manner and certificates is a part of that. Even if you only have an internal facing infrastructure, Citrix XenDesktop requires the vCenter certificate be installed on the Desktop Delivery Controllers for https access to work.
Even if none of these apply to you, surely the pesky certificate warning that every vSphere Client user gets when launching the client is annoying enough to do something about it!
You can click on Install this certificate and do not display any security warnings but this would bypass any certificate checking and each client would need to do this individually.
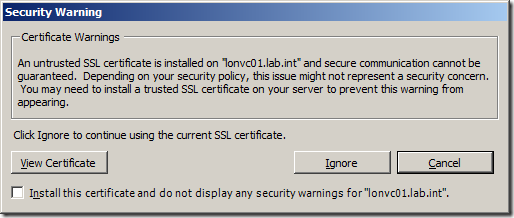
Read more…
One of the challenges with working with HP blades and HP Virtual Connect switches is ensuring all your software and firmware versions are in sync as unfortunately there have been many firmware incompatibility and reliability issues that have plagued the technology over the years and making sure you have firmware that works certainly helps with your sanity!
I’ve been tracking the firmware requirements in my Flex-10 ESX pre-requisites post.
With the release of vSphere 5, things are a little simpler as there is no longer an ESX platform, only ESXi so you don’t have to worry about tracking separate driver requirements for both hypervisor releases.
Read more…

 I have the pleasure today of presenting at the first ever UK VMware User Group. This is a combined meeting of the London, Northern and Scottish VMUGs in the cool National Motorcycle Museum in Solihull which is apparently the “finest and largest motorcycle museum in the world”!
I have the pleasure today of presenting at the first ever UK VMware User Group. This is a combined meeting of the London, Northern and Scottish VMUGs in the cool National Motorcycle Museum in Solihull which is apparently the “finest and largest motorcycle museum in the world”!
My presentation has nothing whatsoever to do with motorcycles unfortunately but is rather about upgrading your virtual infrastructure from vSphere 4 to 5. In hindsight I should have taken some more inspiration from the surroundings and somehow worked a motorcycle angle into my presentation, I should plan more carefully in the future!
Upgrading to vSphere 5 doesn’t actually have to be a particularly complicated procedure if you have all your ducks in a row and understand all the pre-requisites. This is a good thing as it means you can take advantage of all the cool new features without necessarily having to drastically re-architect your vSphere 4 environment but also means some of the old issues like vCenter availability haven’t changed.
Read more…










Recent Comments