VMware has finally officially announced what is to be included in vSphere 6.0 after lifting the lid on parts of the update during VMworld 2014 keynotes and sessions.
See my introductory post: What’s New in vSphere 6.0: Finally Announced (about time!) for details of all the components.
VMware is at last tackling the nightmware of managing vSphere certificates in a more holistic way. Things were relatively simple until VMware started splitting up the compoments of vSphere into multiple components each requiring their own certificate with very particular settings. VMware had released the SSL Certificate Automation Tool which at least attempted to make the installation of the certificates a little easier but it took the perseverance and excellent scripting of Derek Seaman with his certificate series to make the actual process usable.
Customer feedback regarding certificate management has repeatedly highlighted the convoluted process so VMware has finally come up with a solution they believe reduces the operational overhead of managing certificates.
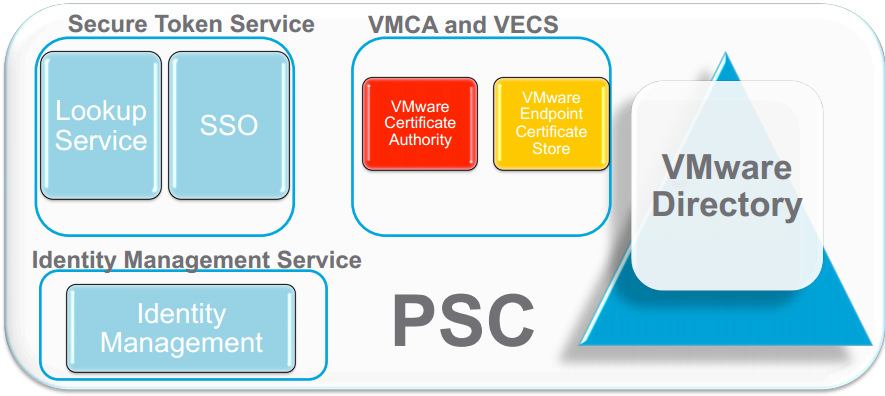
VMware is included two components into the new Platform Services Controller:
The VMware Certificate Authority (VMCA). This is not just a certificate management tool but actually a full blown Certificate Authority in itself. It can provision each ESXi host and each vCenter Server and its associated services with certificates that it signs.
The VMware Endpoint Certificate Service (VECS). This is a service that will store all certificates and private keys for vCenter Server and its associated services.
This means you will no longer have to manually update each separate vCenter component, you can just store all the certs in the VECS and get vCenter to use them.
ESXi host certificates will still be stored locally on each host but can be provisioned from the VMCA.
You don’t have to use the VMCA as a certificate authority or have it in your certificate chain and can choose to use your Enterprise CA or roll your own but you will need to use the VECS to store certs and keys for vCenter.
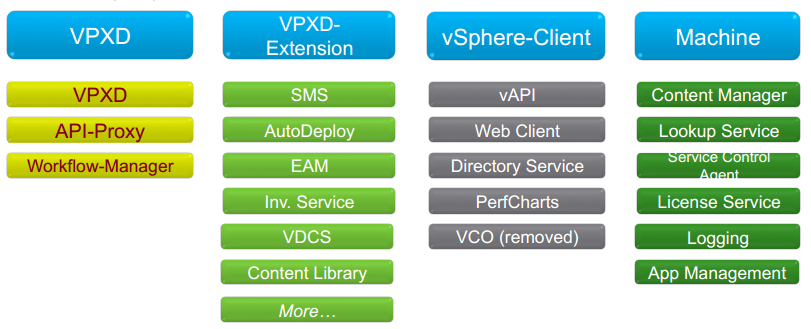
VMware is also simplifying the number of certificates it requires for vCenter internally. vCenter 5.5 needed separate certificates for at least the following:
With vSphere 6.0 there are more components but these components are now being grouped together into what’s being called Solution Users (SU). SUs now hold the certificate for the group rather than each component.
This is what it looks like in the PSC
All the certificate management will be done from a CLI. If you upgrade vCenter or hosts from ESXi 5.x, they will keep their existing certificates.
There are also a number of deployment options:
VMCA Root CA
This is where the VMCA acts as your entire certificate authority and is therefore the simplest deployment. This is the default installation. You will need to trust the VMCA in your browsers to avoid pesky certificate warnings.
Subordinate VMCA
After installation you can make the VMCA a subordinate CA to your Enterprise CA. The VMCA will then mint your certificates which makes the process simpler and itself would be trusted by your enterprise CA.
External CA
After installation, all certificates are replaced from yout Enterprise CA. VMCA will still manage the certificates but it allows you to use your existing Enterprise PKI solution.
Hybrid (VMCA & External)
You can use a hybrid model where the VMCA is created during installation and your vCenter certificates are replaced. YOu can then choose which certificates to replace from your external CA and which to have the VMCA generater. You could for example have all externally facing certificates generated from your Enterprise CA and all the internal hidden from view VMware vCenter service certificates generated by the VMCA.
At last VMware is making certificate management a little easier, to be honest it should have been there when they decided you needed a million very particular certificates for vCenter but I suppose with a rather large development organisation working on different components, common certificates wasn’t high on the priority list, I’m glad it is now.



Recent Comments